Posted by Guest Contributor - Carter Schoenberg on Aug 18th 2025
Mergers and Acquisitions – When Cyber Risk Equals Lower Valuations
Guest Author: Carter Schoenberg (VP, Cybersecurity / Chief Cybersecurity Officer (CSO) at SoundWay Consulting)
In the post-Covid world, a lot has changed about how corporate enterprises conduct their operations. This includes a wide array of cultural aspects, including Cybersecurity considerations. Regulatory influences are becoming increasingly more pervasive as to how businesses are to be held accountable for cybersecurity and data privacy considerations. However, in the realm of Mergers, Acquisitions & Divestitures (MA&D),very little has changed as to how those buying evaluate the target of acquisition’s valuation.
While elements pertaining to earning, revenue, free cash-flow, backlog, recurring revenue, etc. are critical components, very few Private Equity (PE) or Venture Capital (VC) apply prudent criteria/metrics for assessing how cyber/data risk should be factored into a purchase price. Prime examples of these shortcomings are illustrated in the Verizon acquisition of Yahoo as well as Marriott’s purchase of the Starwood Group. Both instances are over a decade old and yet PEs and VCs still tend to focus too heavily on top-end and bottom-end numbers without context of how cyber/data risk can/will negatively impact a purchase price.
Case in point, I am directly familiar with two acquisitions I have participated in whereby playing by the legacy model or risk dramatically impacted the buying organization’s return on investment. In the first example, the purchase of a GRC tool company that had significant technical debt and cyber risk due to a lack or vetting the actual source code beyond running a compiler. The purchase price was $1.2M and the backend cleanup efforts were $842K. That’s a 70% loss on the original investment.
There were no assessments nor considerations for evaluating how this exposure potentially could have reduced the sales price or possibly even result in killing off the deal altogether.
The second acquisition was that of a Managed Security Services Provider (MSSP) with over 80 critical infrastructure clients. Applying lessons learned from the first disaster, recommendations to perform a full static and dynamic source code evaluation were provided. It was denied. The CEO looked at the potential of having 80 recurring revenue clients and that was about it. Furthermore, when pressed whom at the MSSP will be locked in to ensure continuity of operations, the CEO position was, “We do not need to worry about that. What we need to concern ourselves with is how to maximize profit from this transaction.”
Within 30 days of the acquisition, the top two developers quit. Leaving a vacuum of product knowledge and also coming to learn the product was merely open-source software with some proprietary signatures that had never undergone any secure code evaluations. That transaction was $1.4M. Research and development costs, plus improving the security of the proprietary code equated to $625K. A 45% loss on the original investment.
By incorporating key elements from a variety of Security Control Frameworks/Standards like CIS, NIST SP:800-171 or 800-160, could have dramatically changed the target purchase price in ways that could have provided new pathways for consensus between the buyer and seller to terms that are lower than what was originally expected but also reducing the risk to an acceptable level to the buyer.
Merely looking at the threats of the target company means very little without financial context. In Figure 1 below, I demonstrate potential considerations for PE and VC alike.
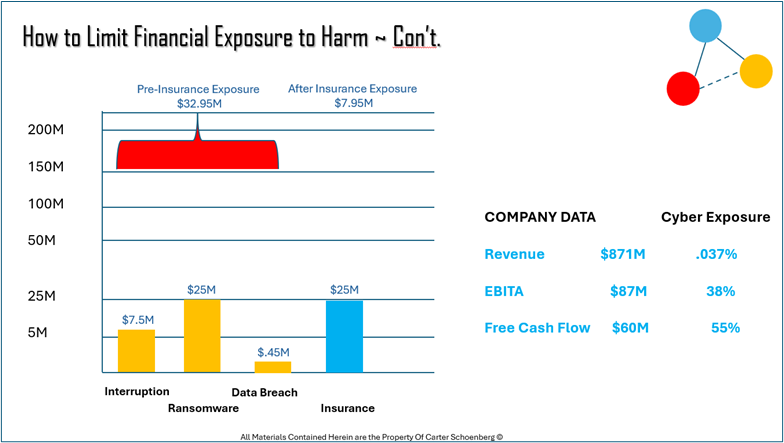
Figure 1 Cyber Risk Evaluations with Context
In Figure 1, the data point “Cyber Exposure” represents the buyer’s side. In many cases when the topic of cyber exposure comes about, metrics like “MODERATE’ or “3.5 out of 10” may come to mind. However, these legacy approaches to cyber risk evaluation offer very little context that are actionable and legally defensible. What is the buyer’s risk appetite. It is not “Moderate” or “High”. It likely needs to be along the lines of “We accept risk reduction measure as long as the measure to not exceed 3% of Revenue.”
Without demonstrating the totalities of exposure in terms of dollars and legal exposure, it is improbable a security case could be made as described in Figure 2.
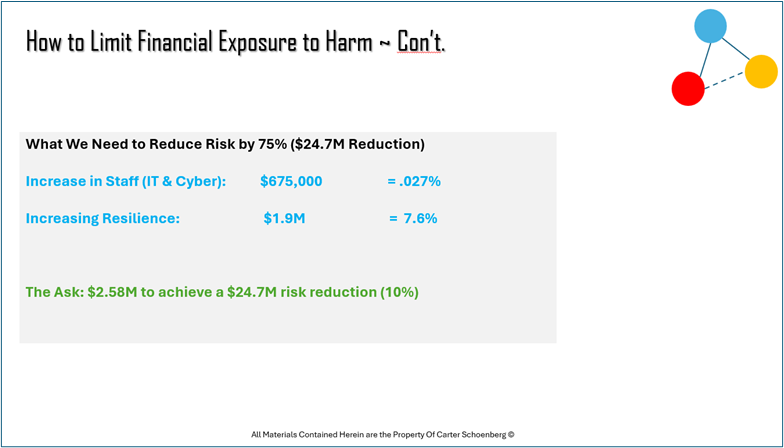
Figure 2 Tallying Cost vs Risk Reduction.
In the scenario depicted, is a $2.58M investment warranted for a $24.7M risk reduction? If the threshold or “appetite” is 3%, then the answer may be “no”. Or it may warrant either 1) an approach to buy down the risk (i.e. lower acquisition price) or 2) assumption of the risk even though its above the previously agreed upon 3% threshold.
In conclusion, cyber risk must be incorporated into the M&A calculus to reduce exposure to harm on the buyer’s side while simultaneously promoting more reasonable and equitable purchase prices in the market.
About the Author
Carter Schoenberg is the Vice President of Cybersecurity and Chief Cybersecurity Officer at SoundWay Consulting, Inc.

