Posted by Guest Contributor - Secure Controls Framework (SCF) on Aug 13th 2025
Why Are NIST CSF Tiers Not A Maturity Model?
Guest Contributor: Secure Controls Framework (SCF)
The NIST Cybersecurity Framework (NIST CSF) is a popular framework to align an organization's cybersecurity practices. However, one component that is nebulous is the inclusion of Tiers in the NIST CSF, where the Tiers are often viewed as a viable Capability Maturity Model (CMM) that can be assessed against. The reality is NIST CSF does not have a traditional CMM, as compared to something like the Systems Security Engineering Capability Maturity Model (SSE-CMM).
What Are NIST CSF Tiers?
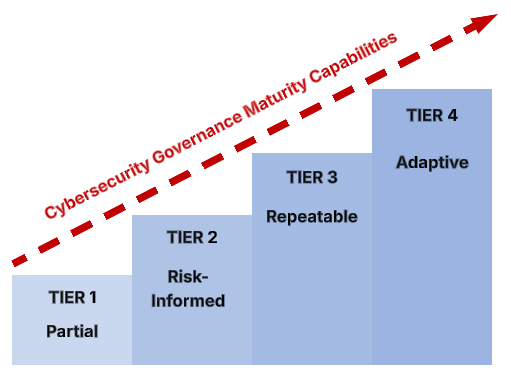
NIST CSF 1.0 introduced the concept of “Implementation Tiers” and was shortened in NIST CSF 2.0 to just “Tier” to describe a current and target (future) level of cybersecurity capability maturity. There are four (4) Tiers in NIST CSF:
- Tier 1 – Partial
- Tier 2 – Risk-Informed
- Tier 3 – Repeatable
- Tier 4 – Adaptive
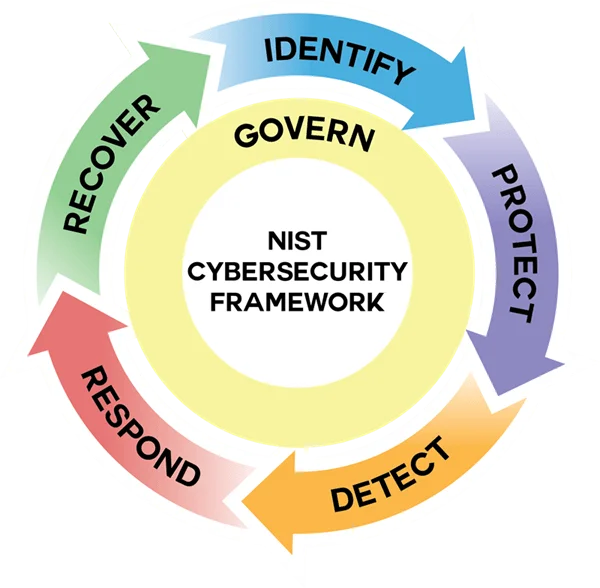
These tiers can be defined as organization-wide or at the function level:
- Govern;
- Identify;
- Protect;
- Detect;
- Respond; and
NIST's stated intent is these Tiers can be applied to an organization’s Profile to characterize the rigor of its cybersecurity risk governance and management practices. The intent is to provide context on how an organization:
- Identifies cybersecurity risks; and
- Implements processes to manage those risks.
Why Are NIST CSF Tiers Not A Traditional Maturity Model?
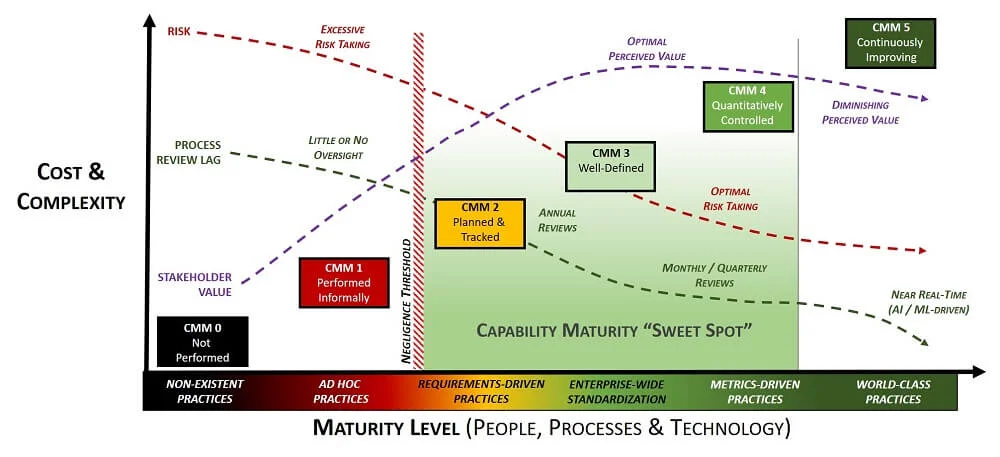
The extent of NIST CSF Tiers being a “maturity model” is the existence of four (4) Tiers that are meant to "reflect a progression from informal, ad hoc responses to approaches that are agile, risk-informed, and continuously improving." There are no defined criteria for the Tiers and that is the glaring weakness of leveraging the NIST CSF Tiers to apply the concept of maturity capability against an organization’s cybersecurity practices.
To compare NIST CSF Tiers to a more traditional CMM, let's take a look at the Cybersecurity & Data Protection Capability Maturity Model (C|P-CMM) that leverages the structure of the SSE-CMM. The C|P-CMM draws upon the high-level structure of the SSE-CMM. These six (6) C|P-CMM levels are:
- CMM 0 – Not Performed
- CMM 1 – Performed Informally
- CMM 2 – Planned & Tracked
- CMM 3 – Well-Defined
- CMM 4 – Quantitatively Controlled
- CMM 5 – Continuously Improving
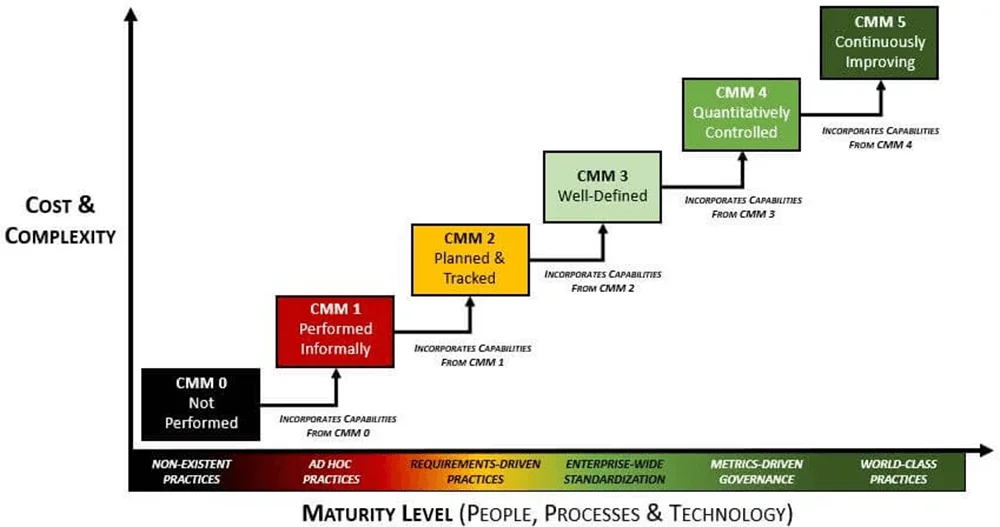
It is possible to make a rough comparison that:
- Tier 1 (Partial) equates to CMM 1 (Performed Informally)
- Tier 2 (Risk Informed) equates to CMM 2 (Planned & Tracked)
- Tier 3 (Repeatable) equates to CMM 3 (Well Defined)
- Tier 4 (Adaptive) equates to CMM 4 (Quantitatively Controlled)
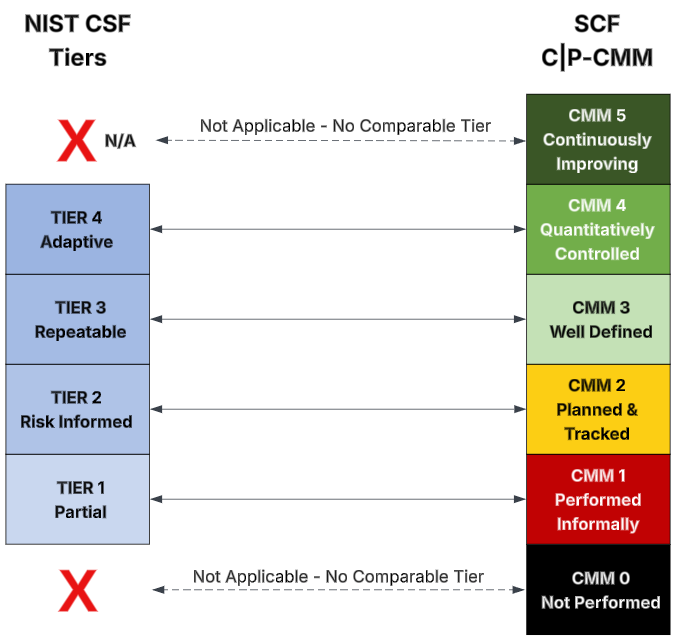
The Tiers within the NIST CSF do not account for capabilities that are non-existent / not performed or continuously-improving controls (e.g., AI / ML-driven changes at near real time). While one could argue that Tier 4 (Adaptive) could address both CMM 4 (Quantitatively Controlled) and CMM 5 (Continuously Improving), it is hard to defend with no authoritative criteria issued by NIST to clearly define how an organization should address Tier alignment.
Maintaining Integrity With Maturity Model Criteria
A “maturity model” is entirely dependent upon the ethics and integrity of the individual(s) involved in the evaluation process. This issue is often rooted in the assessor’s perceived pressure that a control should be designated as being more mature than it is (e.g., dysfunctional management influence). Regardless of the reason, it must be emphasized that consciously designating a higher level of maturity (based on objective criteria) to make an organization appear more mature should be considered fraud. Fraud is a broad term that includes “false representations, dishonesty and deceit.”
This stance on fraudulent misrepresentations may appear harsh, but it accurately describes the situation. There is no room in cybersecurity and data protection operations for unethical parties, so the SCF Council published guidance on what a “reasonable party perspective” should be for maturity criteria evaluation. This provides objectivity to minimize the ability of unethical parties to abuse the intended use of maturity models as part of assessments.