Integrity
NIST defines integrity as, "a property whereby data has not been altered in an unauthorized manner since it was created, transmitted, or stored."
Why Is Integrity A Term GRC Professionals Should Be Familiar With?
Integrity enables situation awareness, where unauthorized or unexpected changes should be detected in real-time, ideally with the capability automatically roll back to a trusted baseline to maintain operational resilience.
An integrity-validating platform should also incorporate whitelisting and file reputation services to differentiate between trusted and suspicious activity while leveraging threat intelligence through STIX and TAXII feeds for an additional layer of proactive defense. Unifying change prevention, automated remediation, and compliance-driven configuration management ensures systems remain secure, resilient, and verifiably trusted in dynamic environments.
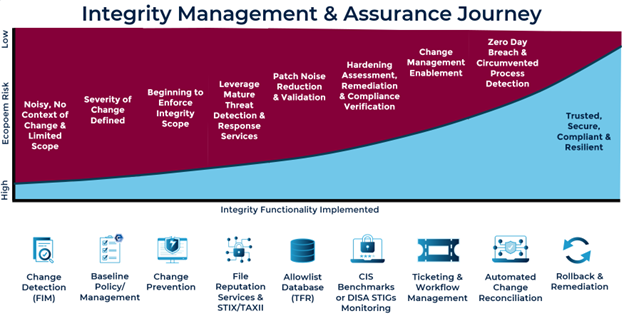
Integrity Management and Assurance
An advanced integrity assurance platform provides continuous visibility and control over critical systems by combining:
- Change detection;
- Configuration monitoring; and
- Policy enforcement.
When a change is detected (ideally in real time), the platform's primary objective is to determine whether the change is good or bad. In doing so, the platform must establish a trusted baseline and enforce configuration compliance while incorporating best practices of system hardening with standards such as CIS Benchmarks and DISA STIGs. Finally, incorporating a ticketing system enables administrators to track, validate, and reconcile changes against an approved change control process, which will uncover both circumvented processes and zero-day malicious activity.
Implementing Integrity Management
Implementing integrity functionality is best approached through a crawl, walk, run maturity model. The crawl phase establishes visibility with change detection and baseline policies. The walk phase integrates configuration management, threat intelligence, allowlisting, and system hardening capabilities. The run phase enables advanced prevention, closed-loop change management, and automated remediation, delivering a trusted, secure, continuous compliant, and resilient infrastructure.
Intengrity Enforcement Benefits
- Reducing MTTI and MTTC – Collapsing the average MTTI (181 days) and MTTC (60 days) to mere seconds.
- Continuous Integrity Assurance – Ensure systems remain trusted and uncompromised.
- Regulatory Compliance – Automate adherence to frameworks like NIST, CIS, DISA STIG, and Zero Trust mandates.
- Operational Resilience – Minimize downtime through rapid rollback and autonomous remediation.
- Enhanced Visibility – Gain real-time insights into all changes across the IT environment.
- Stronger Security Posture – Prevent unauthorized activity while leveraging global threat intelligence.
- Insider Threat Identification – Identify malicious activity from trusted entities within the organization.
Integrity Enforcement Use Cases
- Zero Trust Enablement – Enforce continuous verification and system trustworthiness while meeting NIST 800-207 requirements for Tenet #5.
- Comply-to-Connect – Validate system integrity before allowing network access.
- Regulatory Compliance – Automate adherence to DoD, PCI DSS, HIPAA, SOX, and more.
- Incident Response – Accelerate recovery with forensic capability with unprecedented visibility and awareness.
- Configuration Assurance – Maintain secure and consistent configurations across on-prem, hybrid, and multi-cloud environments.
- Backup and Remediation - Restore to a trusted baseline in seconds, eliminating the need for traditional software backup and reprovisioning, which requires time, energy, money, and downtime.
** SPONSORED CONTENT **
If you are interested in integrity enforcement, take a look at CimTrack from Cimcor:
Real-Time Change Detection
- Monitors critical files, system objects, configurations, and registries in real time.
- Detects unauthorized or suspicious changes across servers, endpoints, databases, network devices, hypervisors, containers, cloud environments, and more.
Baseline Policy Management
- Establishes trusted baselines for files, configurations, and applications.
- Continuously validate system(s) against approved baselines for immediate identification of deviations.
Configuration Management
- Tracks configuration drift and enforces consistency across diverse environments.
- Ensures compliance with operational and security policies.
Change Prevention
- Blocks unauthorized or high-risk changes in real time before they can cause harm.
- Prevents drift from approved policies and standards.
CIS Benchmarks & DISA STIG Alignment
- Provides prebuilt policy templates based on industry standards (CIS Benchmarks, DISA STIGs).
- Automates assessment and reporting against these hardened configuration baselines.
Change Control & Ticketing Integration
- Has its own ticketing capability or integrates with leading ITSM/ticketing systems for streamlined change approval.
- Links detected changes to authorized change requests for full auditability.
Change Reconciliation
- Automatically classifies changes as authorized, unauthorized, or suspicious.
- Reconciles detected changes with approved change management processes.
Whitelisting Capabilities
- Creates trusted file and configuration whitelists for tighter enforcement.
- Ensures only validated and approved objects are permitted to run.
File Reputation Services
- Enriches detection with real-time threat intelligence from file reputation databases.
- Flags and isolates files associated with known vulnerabilities or malware.
STIX/TAXII Threat Intelligence Feeds
- Ingests structured threat intelligence (STIX/TAXII) for proactive defense.
- Correlates detected changes with emerging threat indicators for faster response.
Rollback & Remediation
- Instantly restores altered files, configurations, or registry settings to a trusted state.
- Provides granular rollback capability to ensure system integrity and availability.
