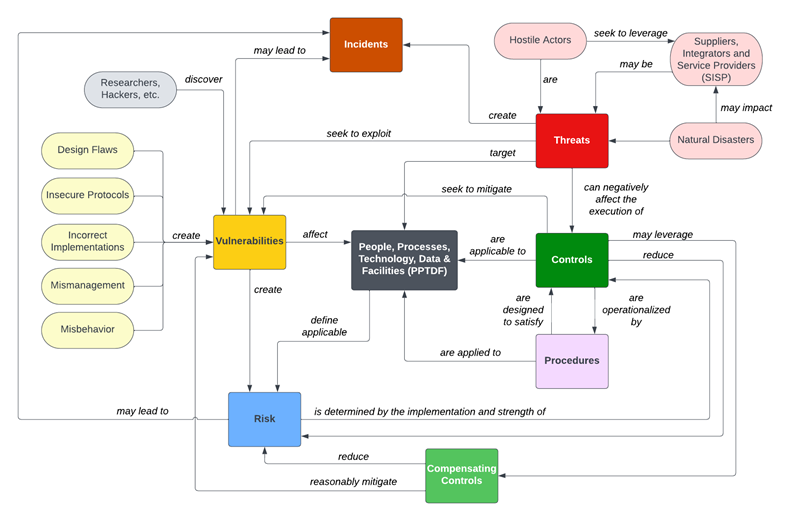
Risks vs Threats
In GRC operations, words have specific meanings. The concept of inheritance vs reciprocity is a common "word crimes" incident.
- Threat. A person or thing likely to cause damage or danger (noun) or to indicate impending damage or danger (verb).
- Risk. A situation where someone or something valued is exposed to danger, harm or loss (noun) or to expose someone or something valued to danger, harm or loss (verb).
- Vulnerability. A weakness in an information system, system security procedures, internal controls, or implementation that could be exploited or triggered by a threat source.
- Control. The safeguards or countermeasures prescribed for an information system or an organization to protect the confidentiality, integrity, and availability of the system and its information.
- Compensating Control. The security controls employed in lieu of the recommended control(s) that provide equivalent or comparable protection for an information system or organization.
- Procedure. A set of instructions used to describe a process or procedure that performs an explicit operation or explicit reaction to a given event. The design and implementation of a procedure must be reasonable and appropriate to address the control.
- Reasonable. Appropriate or fair level of care. This forms the basis of the legal concepts of "due diligence" and "due care" that pertain to negligence.
- Mitigate. To make less severe or painful or to cause to become less harsh or hostile.
Understanding The Interaction Between Threats, Vulnerabilities, Risks, Controls, Incidents and more!