Laws, Regulations & Frameworks (L/R/F)
Of the common GRC terms are routinely abused, the concept of laws, regulations and frameworks is close to the top of the list. Words have meaning and in compliance-related settings, misunderstandings can have negative ramifications. Cybersecurity, IT and privacy professionals routinely abuse the terms “law” and “regulation” as if they are synonymous, but those terms have unique meanings that need to be understood.
Cybersecurity Laws / Regulations / Frameworks (L/R/F) - The Basis of GRC
It serves both cybersecurity and IT professionals well to understand the compliance landscape, since they can present issues of non-compliance in a compelling business context to get the resources you need to do their job. Beyond just using terminology properly, understanding which of the three types of compliance is crucial in managing both cybersecurity and privacy risk within an organization. The difference between non-compliance penalties can be as stark as:
- Going to jail;
- Getting fined;
- Getting sued;
- Losing a contract (breach of contract); or
- An unpleasant combination of the previous options.
Laws, Regulations and Frameworks Help Establish "Must Have" vs "Nice To Have" Requirements
When discussing cybersecurity and data privacy requirements, the term "must" is often thrown around as an absolute. This is most often due to an applicable law, regulation or contract clause that is compelling the control to exist.
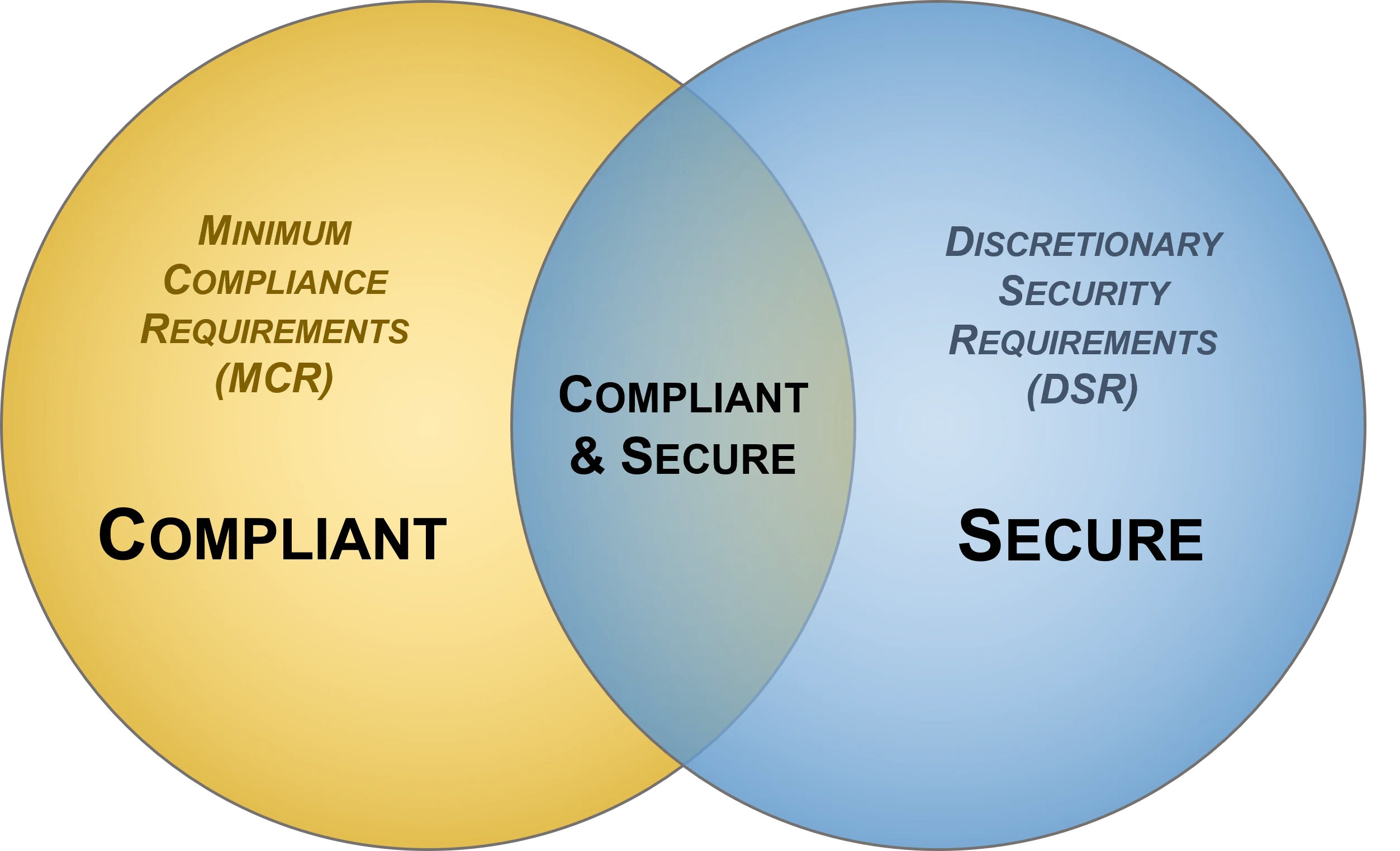 |
There is a need to understand and clarify the difference between "compliant" versus "secure" since that is necessary to have coherent risk management discussions. To assist in this process, it helps an organization to categorize its applicable controls according to “must have” vs “nice to have” requirements:
|
Secure and compliant operations exist when both MCR and DSR are implemented and properly governed:
- MCR are primarily externally-influenced, based on industry, government, state and local regulations. MCR should never imply adequacy for secure practices and data protection, since they are merely compliance-related.
- DSR are primarily internally-influenced, based on the organization’s respective industry and risk tolerance. While MCR establish the foundational floor that must be adhered to, DSR are where organizations often achieve improved efficiency, automation and enhanced security.
What Are Cybersecurity Laws?
Laws are statutory obligations. From a cybersecurity and data privacy perspective, common cybersecurity laws include, but are not limited to:
US - Federal Laws
- Children's Online Privacy Protection Act (COPPA);
- Fair and Accurate Credit Transactions Act (FACTA) - including "Red Flags" rule;
- Family Education Rights and Privacy Act (FERPA);
- Federal Information Security Management Act (FISMA);
- Federal Trade Commission (FTC) Act;
- Gramm-Leach-Bliley Act (GLBA);
- Health Insurance Portability and Accountability Act (HIPAA); and
- Sarbanes-Oxley Act (SOX).
US - State Laws
- California SB 1386;
- California Consumer Protection Act (CCPA) / California Privacy Rights Act (CPRA)
- Massachusetts 201 CMR 17.00;
- Oregon ORS 646A.622; and
- Texas SB 2610.
International Laws
- Canada - Personal Information Protection and Electronic Documents Act (PIPEDA);
- EU - General Data Protection Regulation (GDPR) (note - it says "regulation" but it is a law in the EU);
- UK - Data Protection Act (DPA); and
- Other countries' variations of Personal Data Protect Acts (PDPA).
What Are Regulatory Cybersecurity Requirements?
Regulatory obligations are required by law, but are rules issued by a regulating body (e.g., government agency). Regulatory requirements tend to change more often than statutory requirements, due to how difficult it can be to change a law. From a cybersecurity and data privacy perspective, common regulatory requirements include, but are not limited to:
US Regulatory Requirements
- Defense Federal Acquisition Regulation Supplement (DFARS);
- Cybersecurity Maturity Model Certification (CMMC);
- Federal Acquisition Regulation (FAR);
- DoD Information Assurance Risk Management Framework (DIARMF);
- National Industrial Security Program Operating Manual (NISPOM);
- Financial Industry Regulatory Authority (FINRA); and
- New York Department of Financial Services (NY DFS) 23 NYCRR 500.
What Are Cybersecurity Frameworks?
A cybersecurity framework provides structure to build capabilities to be secure, compliant and/or resilient. There are many frameworks available from both private and public sources, each with its own level of detail, focus and structure. Organizations tend to adopt a framework to serve as a blueprint to address their security, compliance and resilience needs. It is common for organziations to blend multiple frameworks or use a metaframework (a framework of frameworks) to address their unique requirements. From a cybersecurity and data privacy perspective, common cybersecurity frameworks include, but are not limited to:
- Secure Controls Framework (SCF);
- CIS Critical Security Controls (CIS CSC);
- CSA Cloud Controls Matrix (CSA CCM);
- AICPA Trust Services Criteria (TSC);
- Generally Accepted Privacy Principles (GAPP);
- NIST Cybersecurity Framework (NIST CSF);
- NIST SP 800-53;
- NIST SP 800-161;
- NIST SP 800-171;
- NIST AI 100-1;
- NIST AI 600-1;
- ISO 27001 / 27002;
- ISO 42001; and
- Many, many more!
What Are Cybersecurity Metaframeworks?
A cybersecurity metaframework is a "framework of frameworks" - it is essentially a hybrid model to cover multiple laws, regulations and frameworks. The three (3) leading metaframeworks in the cybersecurity industry include:
- Secure Controls Framework (SCF);
- Unified Compliance Framework (UCF); and
- HITRUST.
What Are Contractual Cybersecurity Requirements?
Contractual cybersecurity requirements are contractual obligations between two or more organizations . A contractual obligation may be as simple as a cybersecurity or data privacy addendum in a vendor contract that calls out unique requirements. It also includes broader requirements from an industry association that membership brings certain obligations. From a cybersecurity and data privacy perspective, common contractual compliance requirements include, but are not limited to:
- Payment Card Industry Data Security Standard (PCI DSS) compliance;
- ISO 27001 certification;
- Service Organization Control (SOC) audits; and
- HITRUST certification.
** SPONSORED CONTENT **




