How To GRC
GRC is not meant to be a "free for all" event where Governance, Risk and Compliance teams operate in silos. It is meant to be a unified approach to ensuring the organization is secure, compliant and resilient. What does this mean in practical terms:
- Compliance defines the "must have" and "nice to have" requirements based on external and internal factors.
- Governance develops the internal controls necessary for the organization to have sufficient evidence of due diligence and due care to withstand scrutiny from an external party (e.g., assessor, auditor, regulator, insuror, prosecuting attorney, etc.).
- Risk leverages the scope and requirements established by Compliance and Governance to maintain situational awareness, including Third-Party Risk Management (TPRM) practices.
How To Do Governance, Risk & Compliance (GRC)
All too often, this approach breaks down for a myriad of reasons (e.g., ignorance, scope creep, reorganizations, business process changes, etc.). When that happens, it is common to find:
- Compliance is unware of what the statutory, regulatory and contractual obligations are, since it is left out of pertinent business planning discussions. This exposes the organization to legal risks due to non-compliance.
- Governance maintains practices and documentation that are insufficient to address its actual needs (e.g., following a specific set of requirements, when it is legally obligated to implement more robust practices).
- Risk "goes rogue" and creates its own TRPM questions that have nothing to do with the organization's actual policies, standards and controls. This is where risk management teams create TRPM questions and try to hold suppliers to requirements that are actually more restrictive and robust than the organization has for itself.
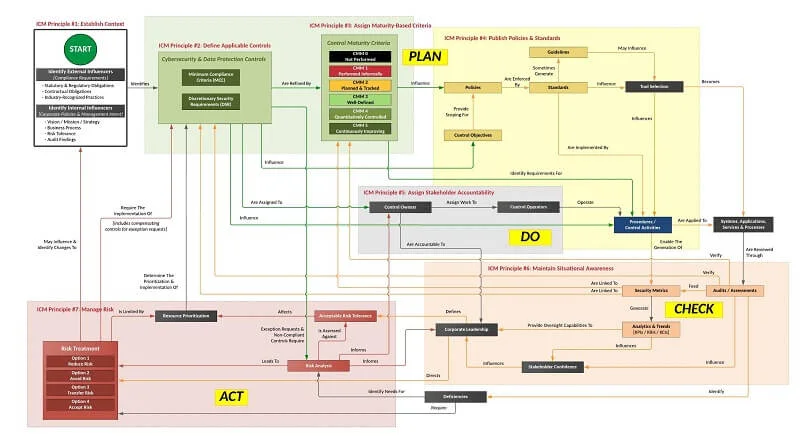
Take A Plan, Do, Check & Act Approach To GRC
A comprehensive view towards governing a cybersecurity & data privacy program is necessary to avoid the pitfalls discussed above. Without an overarching concept of operations for the broader GRC function, organizations will often find that their governance, risk, compliance and privacy teams are siloed in how they think and operate. These siloed functions and unclear roles often stem from a lack of a strategic understanding of how these specific functions come together to build a symbiotic working relationship between the individual teams that enables quality control over people, processes and technology.
Utilizing a Plan, Do, Check & Act (PDCA) approach that is a logical way to design a governance structure:
- Plan. The overall GRC process beings with planning. This planning will define the policies, standards and controls for the organization. It will also directly influence the tools and services that an organization purchases, since technology purchases should address needs that are defined by policies and standards.
- Do. Arguably, this is the most important section for cybersecurity & data privacy practitioners. Controls are the “security glue” that make processes, applications, systems and services secure. Procedures (also referred to as control activities) are the processes how the controls are actually implemented and performed. The Secure Controls Framework (SCF) can be an excellent starting point for a control set if your organization lacks a comprehensive set of cybersecurity & data privacy controls.
- Check. In simple terms, this is situational awareness. Situational awareness is only achieved through reporting through metrics and reviewing the results of audits/assessments.
- Act. This is essentially risk management, which is an encompassing area that deals with addressing two main concepts (1) real deficiencies that currently exist and (2) possible threats to the organization.